感谢9年的陪伴,江湖再见!!!
标签
-
privilege
exe
友情链接
清理
eYou
内存破坏
验证码
DOUPHP
PHPCMS
cmseay
getshell
重装
Mao10CMS
LebiShop
PHPB2B
越权
骑士人才
用友NC-IUFO
360webscan
ecshop
真实IP
POC
MS15-002
cdn
dz
php云人才
读取
任意
Data地方门户
安全报告
上传
通达oa
云购CMS
ThinkPHP
大米cms
爆路径
UWA
uckey
本地
溢出
linux
unserialize
WhatsApp
PHPMyWind
齐博CMS
安全狗绕过
后门
反向代理
phpok
用友
open_basedir
php5
xae
tnftp
FreeBSD10
MacOS
全自动
苹果cms
安卓
窃听
绕过
sql注入
程氏舞曲
存储性xss
骑士cms
网马
远程执行
IE
cmseasy
web漏洞
扫描器
小马
一句话木马
注入
歌曲
D盾
一句话
2014-4113
windows本地提权
提权
箱子
windows2003登陆界面
窃取cookies
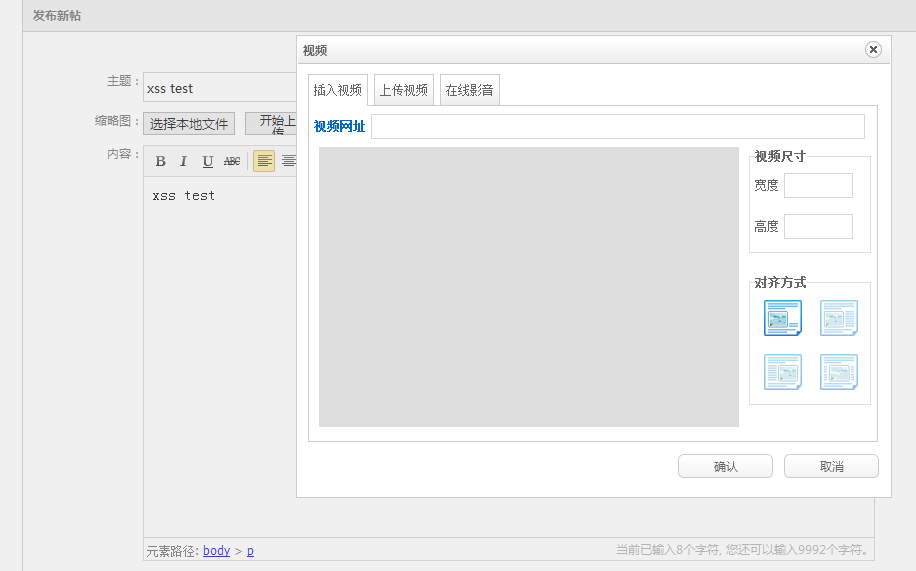
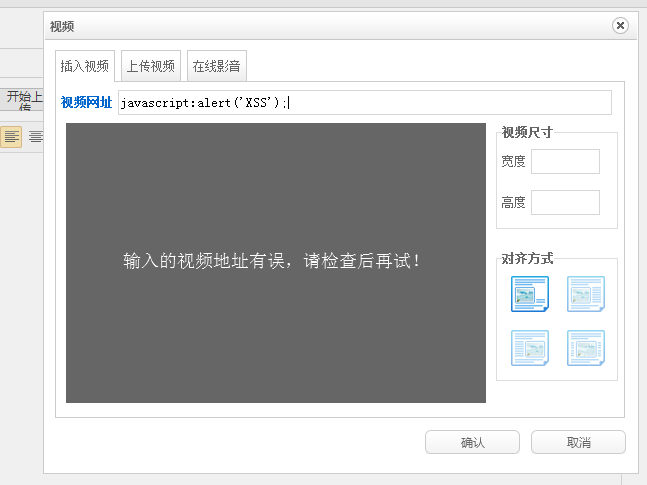
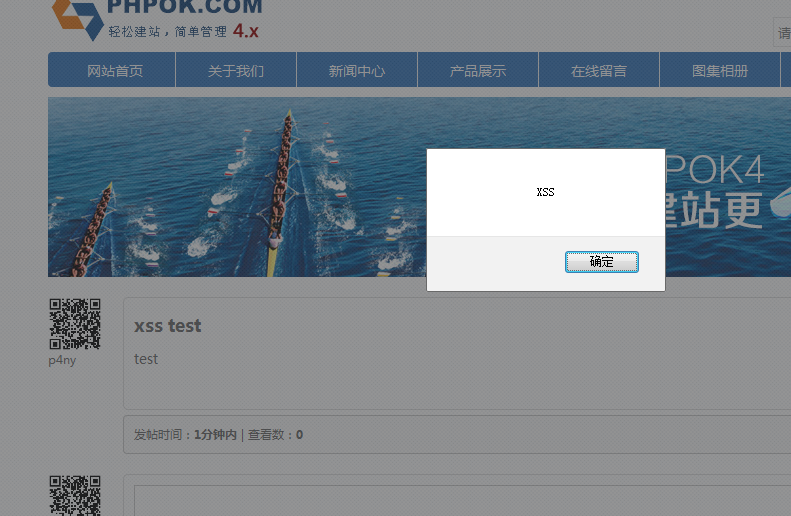
xss
img标签
ShellShock
社工库
社工
卡通人物
卡通人物长大后
童年
免费空间
远程命令执行
HFS
url采集
旁注
识别
php免杀
比特儿
扫号